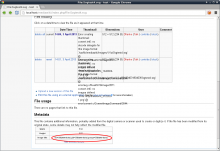
Reported by Daniel Franke. Verified this on my dev system (recent git pull) with the poc svg.
Hello Wikimedia security folks:
I've just discovered a vulnerability in Mediawiki's SVG metadata
extraction feature which enables an attacker to achieve remote file
inclusion and, in some cases, remote code execution. I've developed a
proof-of-concept exploit against mediawiki-1.19.4 as distributed with
Debian Wheezy, but suspect that the same exploit will work against all
recent versions.
The nature of the vulnerability is that the XMLReader instance used in
SVGMetadataExtractor.php performs expansion of XML external entities
(XXEs). As a result, if an attacker uploads an SVG file such as the
following:
<!DOCTYPE svg [
<!ENTITY foo SYSTEM "file:///etc/passwd">
]>
<svg xmlns="http://www.w3.org/2000/svg" version="1.1">
<desc>&foo;</desc> <rect width="300" height="100"
style="fill:rgb(0,0,255);stroke-width:1;stroke:rgb(0,0,0)" />
</svg>
then Mediawiki will read from /etc/passwd and expose its contents in
the 'Metadata' section of the image page created as a result of the
upload.
If PHP's 'expect' extension is enabled, the same technique can be used
to achieve remote code execution by giving an expect:// URL as the
system identifier for the external entity.
I've attached a screenshot demonstrating remote code execution, having
uploaded an SVG file like the one above, but with "expect://id"
replacing "file:///etc/passwd".
There may possibly be other exploit vectors with weaker preconditions,
but the following conditions are necessary in order for this
particular exploit to succeed:
- File upload must be enabled.
- $wgFileExtensions[] must include 'svg'.
- $wgSVGConverter must be set to something other than 'false'.
- To directly achieve remote code execution, PHP's 'expect' extension
(http://pecl.php.net/package/expect) must be installed and enabled.
You should be able to close this vulnerability by calling
'libxml_disable_entity_loader()' prior to doing any parsing. Loading
external entities is almost never desirable, so I suggest doing this
globally, not just from SVGMetadataExtractor.php.
For more information on XXE vulnerabilities in general, see
http://www.securityfocus.com/archive/1/297714.
Version: unspecified
Severity: normal